IPSec高可靠性技术
IPSec VPN高可靠性概述:
IPSec隧道由网络设备和链路组成,设备故障或者链路故障都会导致IPSec隧道中断,存在单点故障。因此在设计IPSec VPN高可靠性时既要考虑保护链路,也需要考虑保护网络设备。
IPSec高可靠性设计可以分为两类,一种是链路冗余,另一种是主备网络备份。其中链路冗余可以分为主备链路备份和隧道化链路备份。
解决链路单点故障
解决方案概述:
多链路两种思路:
A. 链路的主备方式
2:1模式 2:2 模式
B.隧道化的备份 —-华为建议
通过Tunnel接口进行链路冗余备份可以实现多条链路的冗余备份,而且与主备链路冗余备份相比,配置更简单,流量切换速度更快。
主备链路模式缺点:当主链路DOWN以后切换至备份链路需要重新触发IKE SA IPSEC SA,造成业务中断
隧道备份方式
- 优点:当物理接口DOWN了,不影响IPSEC隧道的SA,不会影响业务的中断
- 缺点:隧道接口需要一个公网IP地址。
IPSec 主备链路备份配置示例:
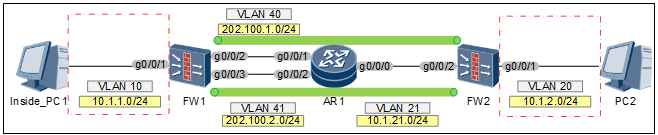
2:1模式的配置思路:
1 | 2端 |
测试检查:
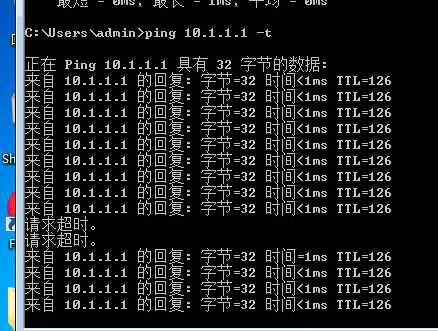
注意:在主备链路备份下当链路发生切换时,会造成丢包。所以建议用隧道模式。
主备链路模式缺点:当主链路DOWN以后切换至备份链路需要重新触发IKE SA IPSEC SA,造成业务中断
IPSec 隧道化链路备份配置 ——–华为建议 :
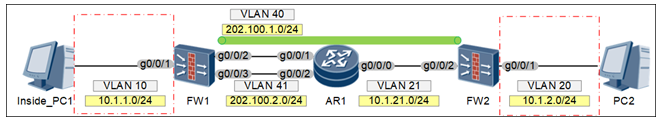
配置思路:
1 | 第一步:配置IPSEC VPN |
注意:隧道地址必须是公网地址,可达的。
总结:隧道备份方式
优点:当物理接口DOWN了,不影响IPSEC隧道的SA,不会影响业务的中断
缺点:隧道接口需要一个公网IP地址。
解决设备单点故障
解决方案概述:
- 双机单ISP,可能会存在一个运营商链路故障
- 双机双ISP,最终完美解决方案。
IPSec 双机热备主备备份配置:
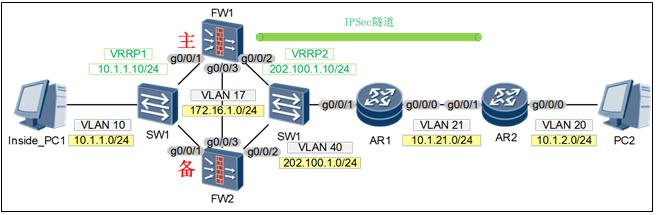
配置思路:
1 | 第一步:配置双机热备 |
双机单ISP缺点:链路故障
参考文档:华为HedEx文档

