其他文章:
tacacs+协议报文抓包示例
如果使用wireshark对tacacs+报文进行抓包,需要将tacacs+服务器的tac_plus服务监听端口设置为49,这是为tacacs+分配的默认端口,TCP 49。
此时,会将TCP 49端口的报解码为tacacs+报文。否则,看到的都是TCP交互报文。
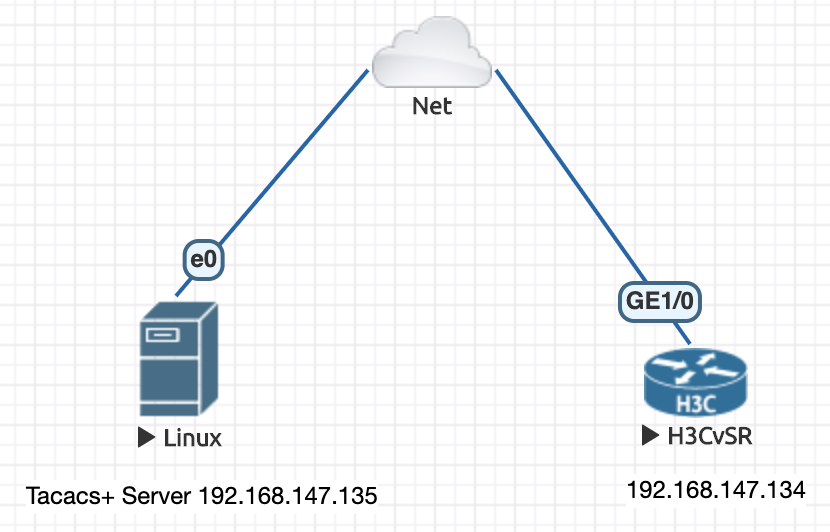
实验拓扑:
本次实验在eve-ng仿真环境中进行测试,可测试H3C,华为,Arista,Cisco设备。
图中Linux运行CentOS7系统,安装了Tacacs+守护进程,监听192.168.147.135 TCP 49端口。
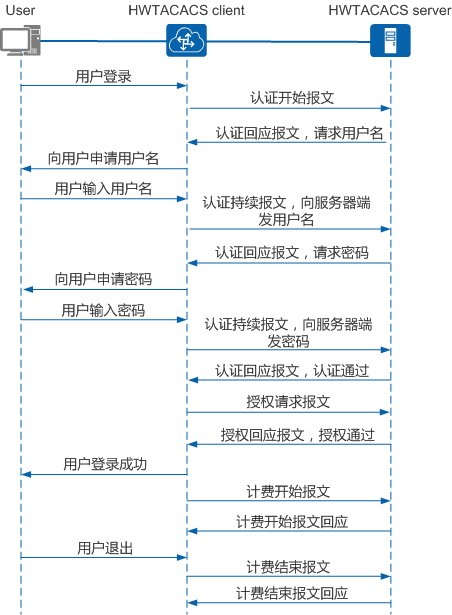
Tacacs+报文交互流程图:
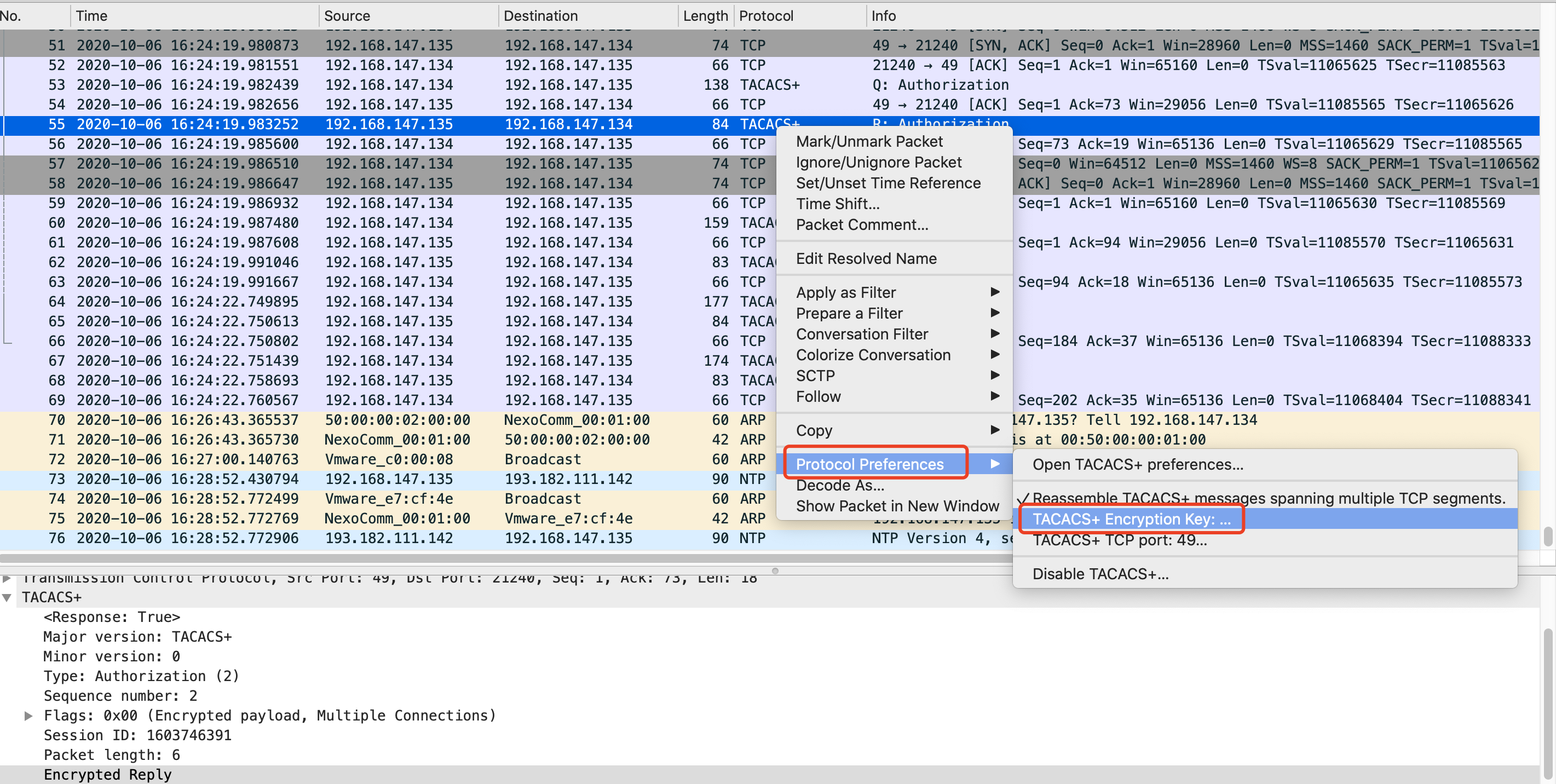
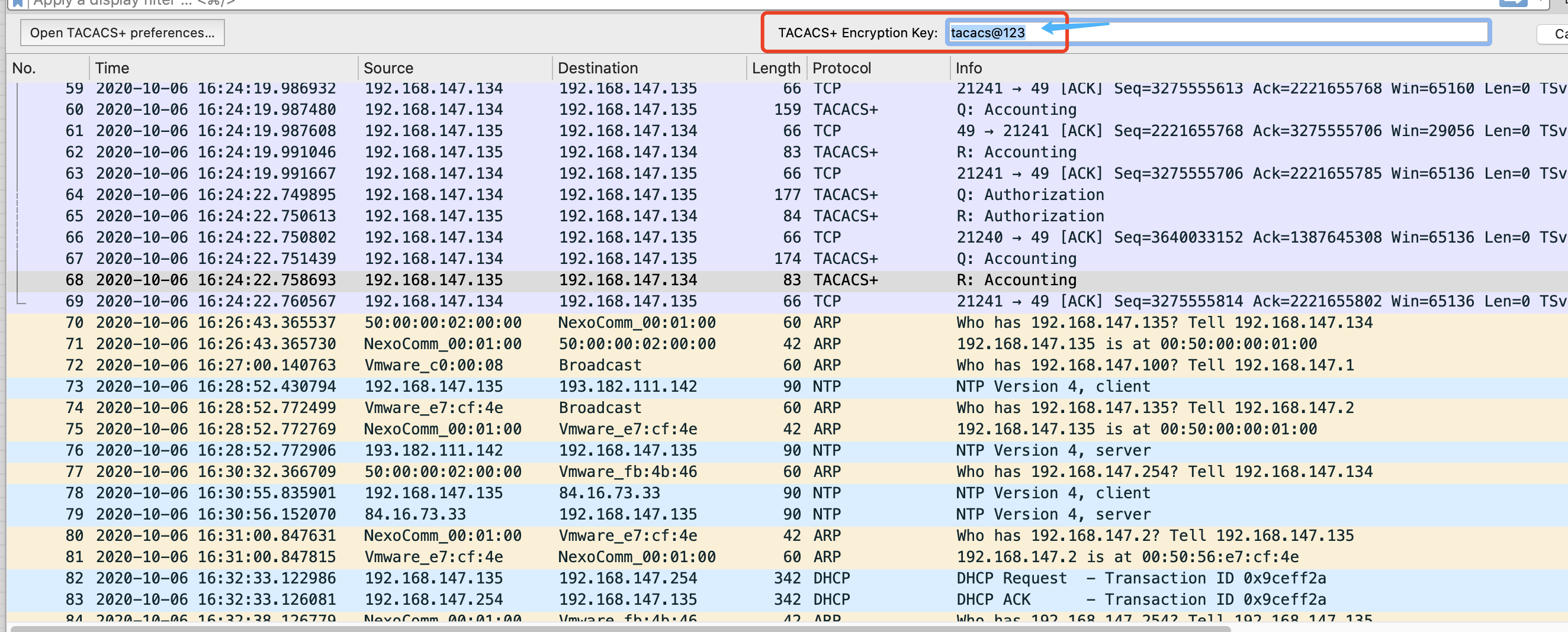
注意:在wireshark中抓的tacacs+报文默认为加密报文,无法看到详细的报文内容,需要在wireshark中输入tacacs+密钥进行解密,从而可以查看报文内容。
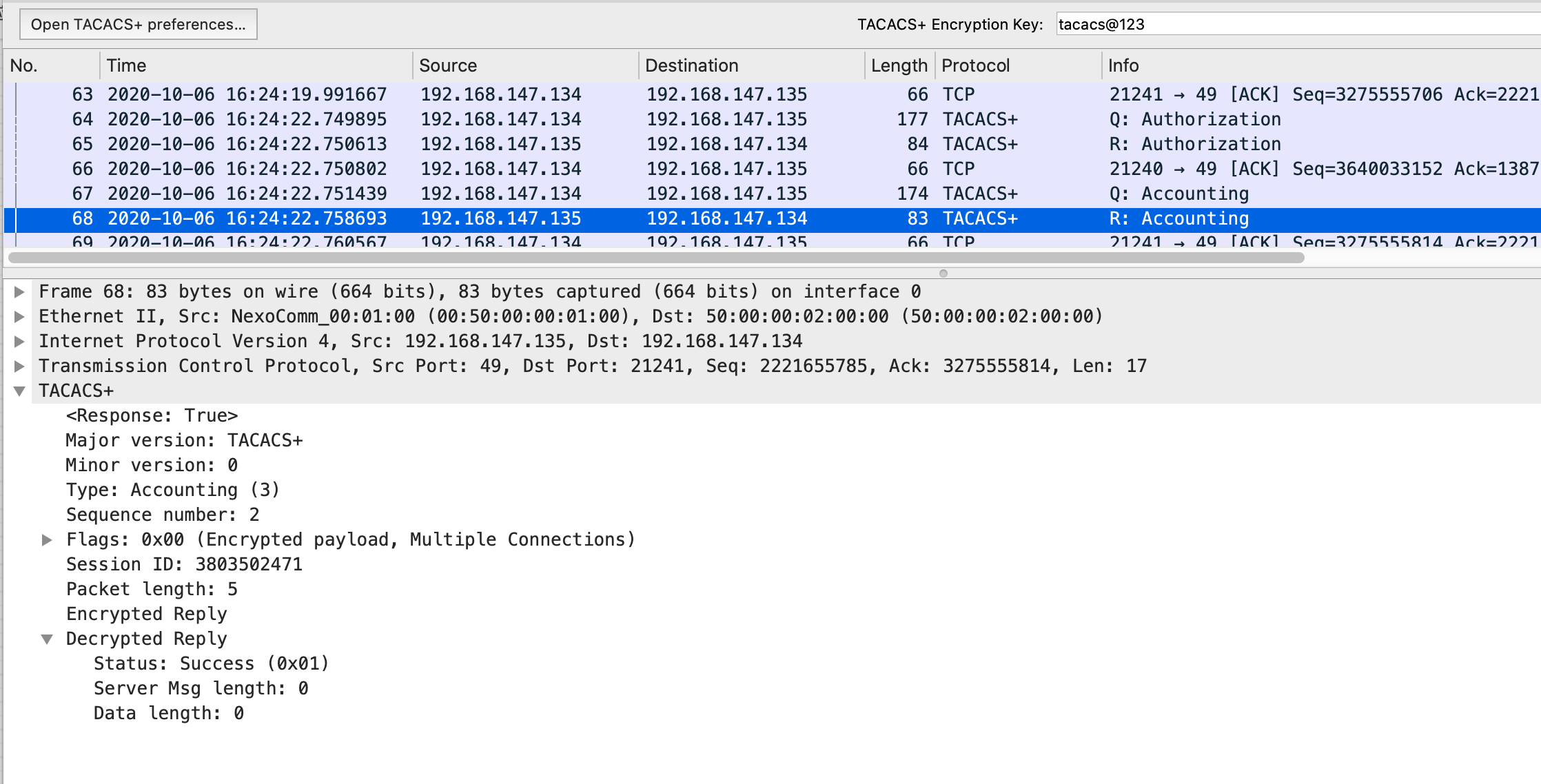
操作步骤:选择tacacs+协议报文,右键选择Protocol Preferences, 选择,TACACS+Encryption Key
输入Tacacs+服务器密钥即可解密报文。
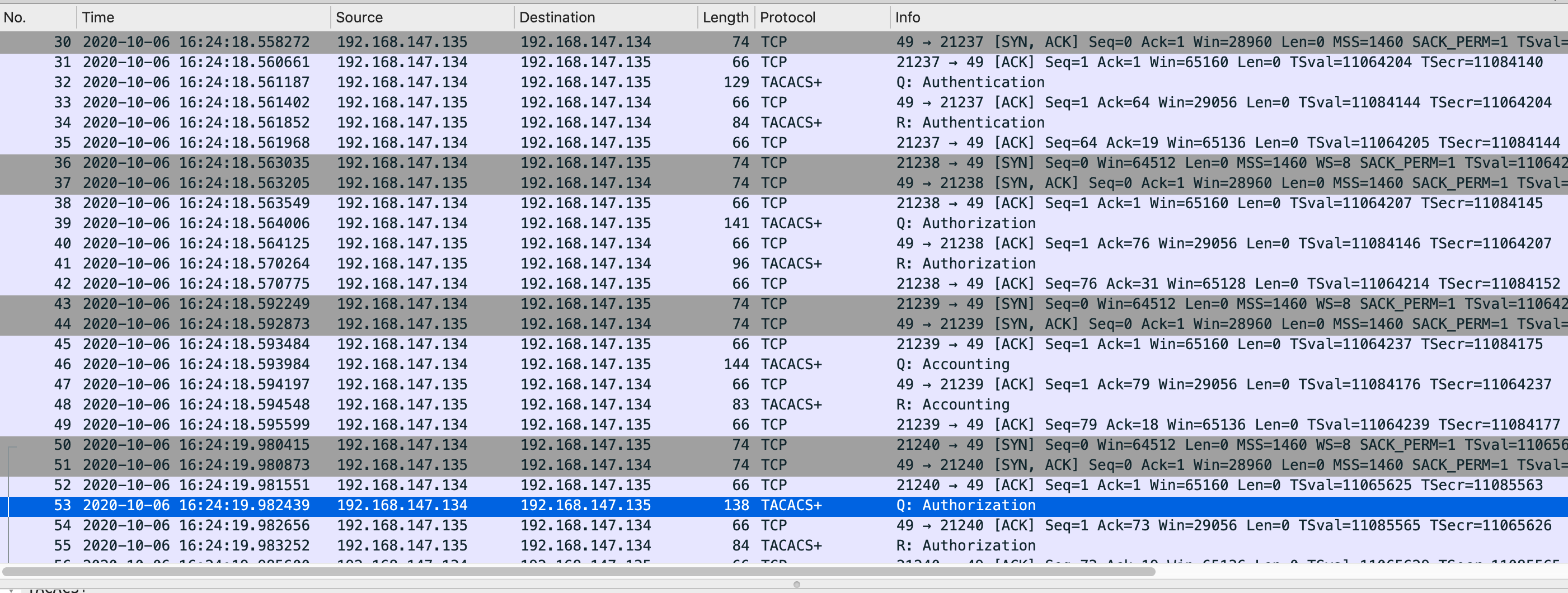
Authentication报文抓包示例:
认证请求报文:
如下图,当用户远程登陆交换机时,交换机会将用户名,密码都发给tacacs+服务器,进行认证请求。
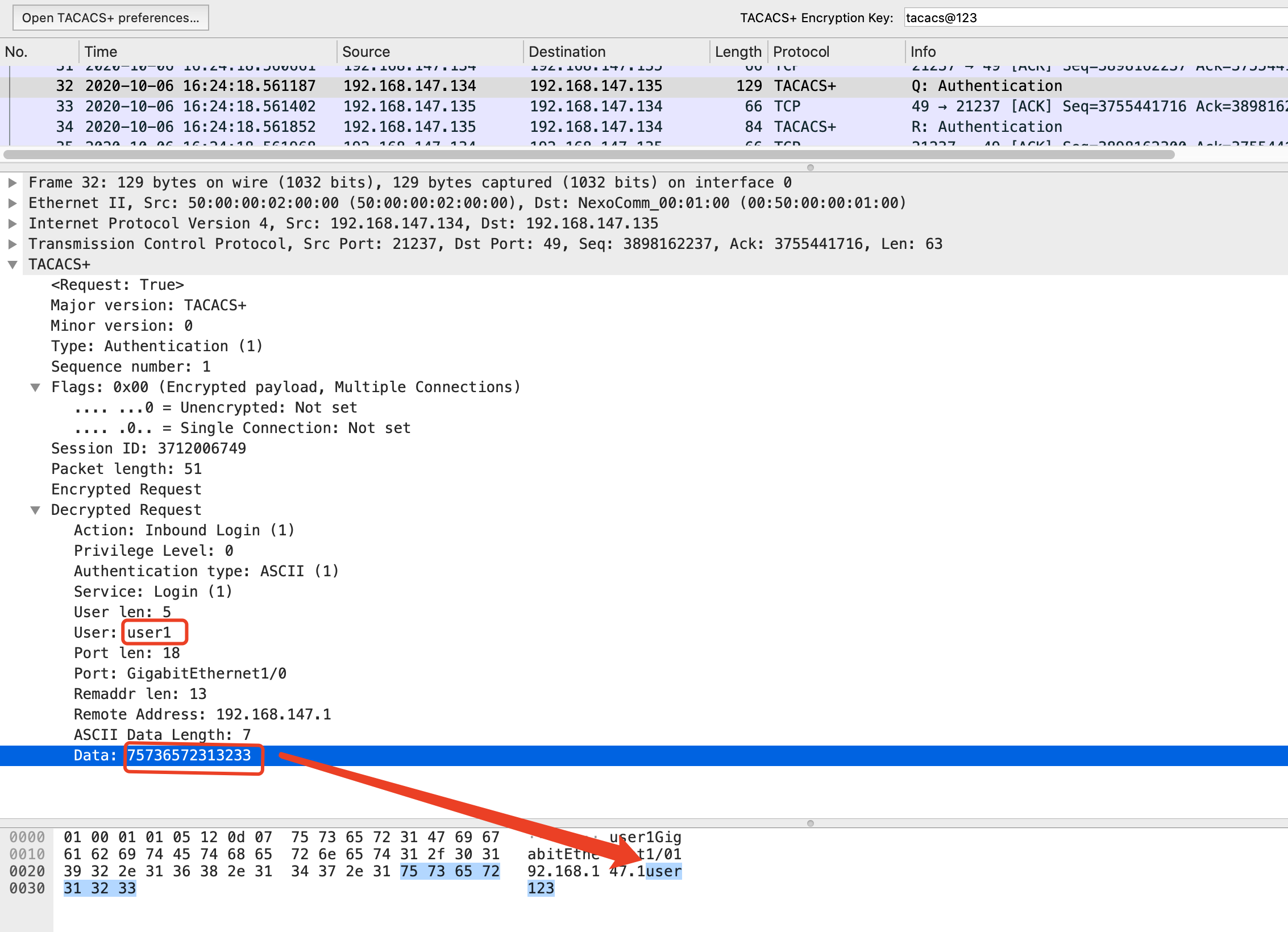
认证回应报文:
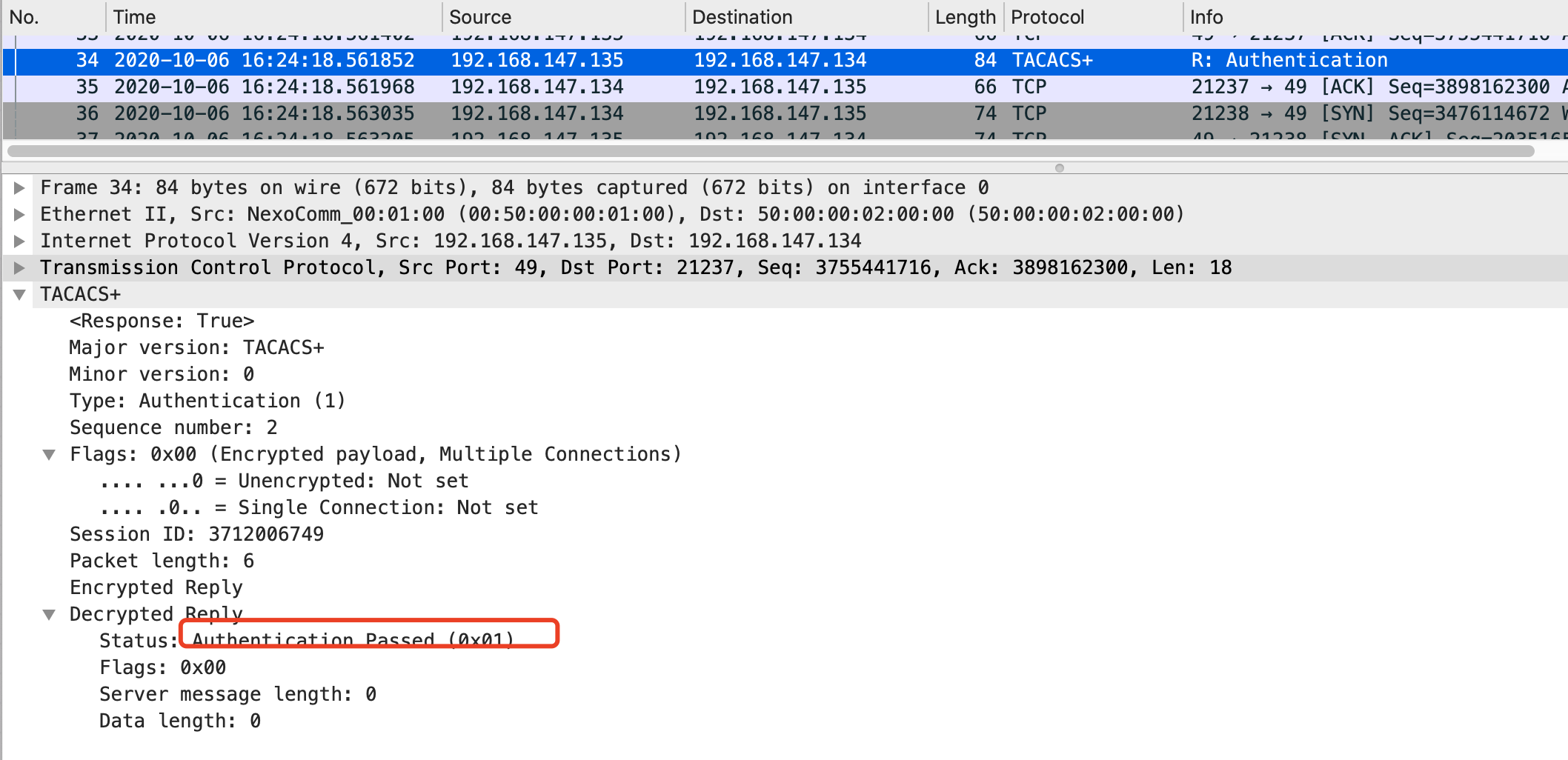
Tacacs+服务器收到交换机的认证请求报文后,如果账号密码都正确,则返回认证回应报文,里面表明认证通过。
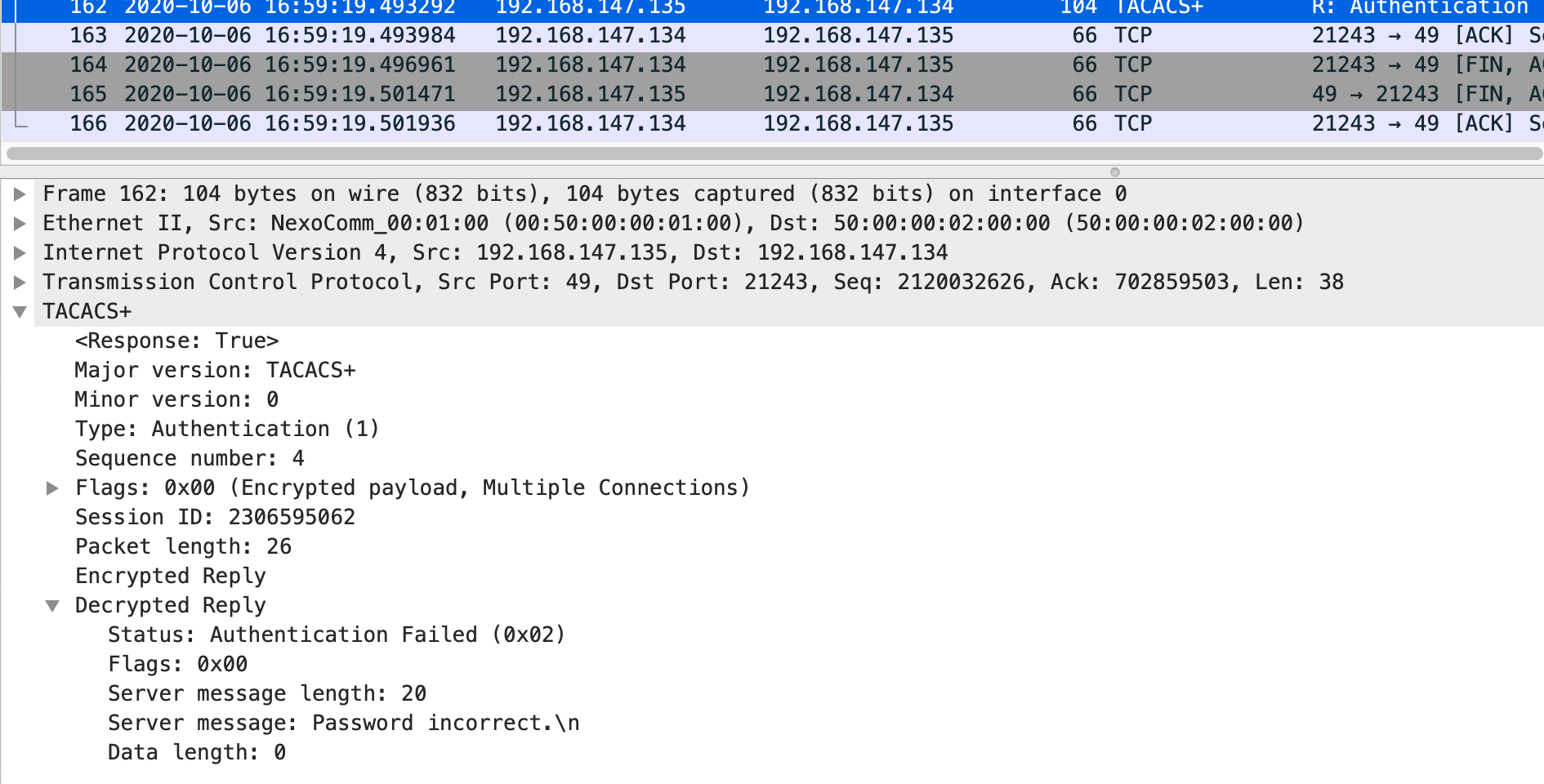
如果账号或密码不正确,则返回认证失败报文。
Authorization报文抓包示例:
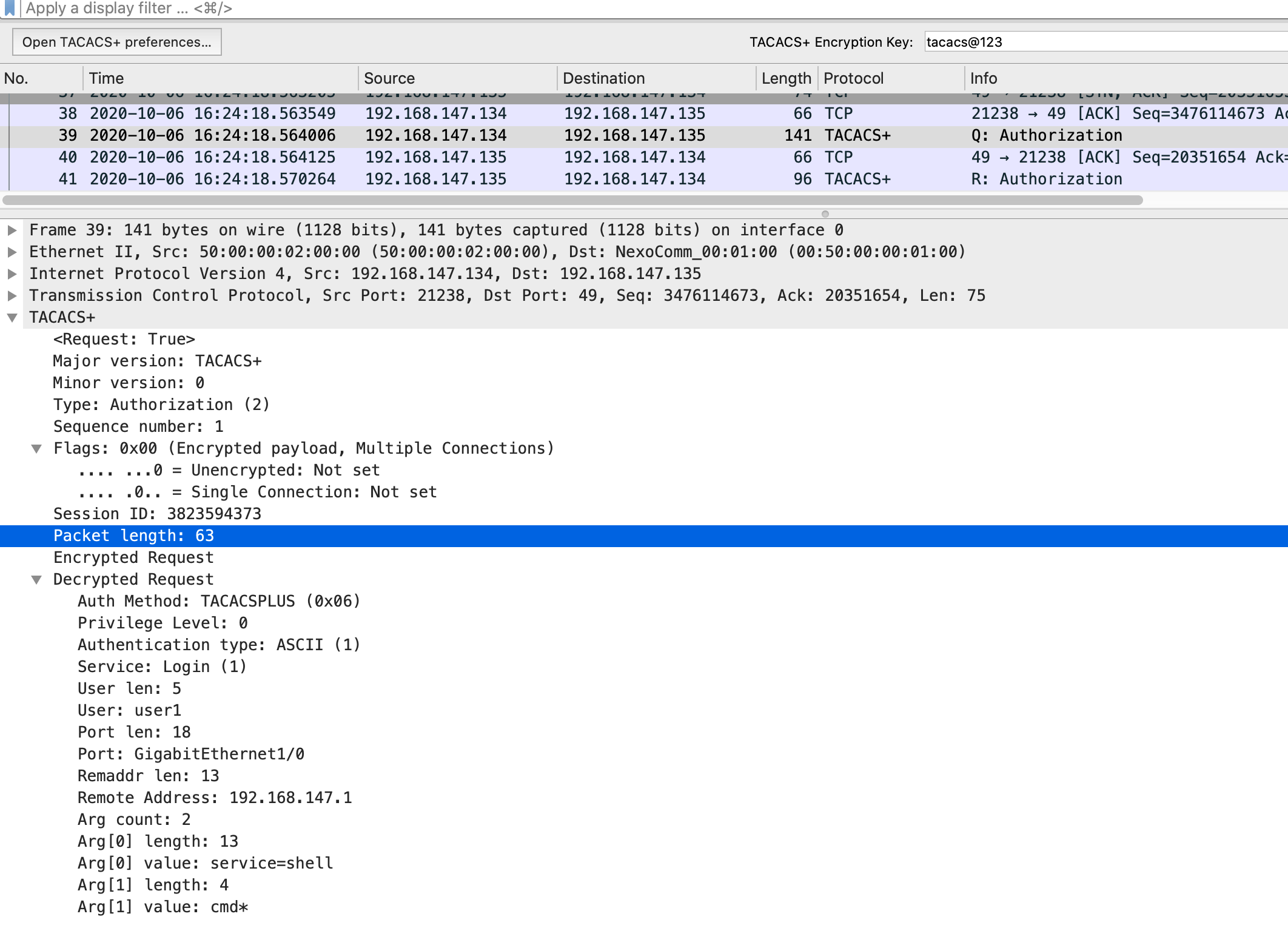
授权请求报文:
在认证成功之后,交换机会发起授权请求报文,携带service类型,需要授权的命令。
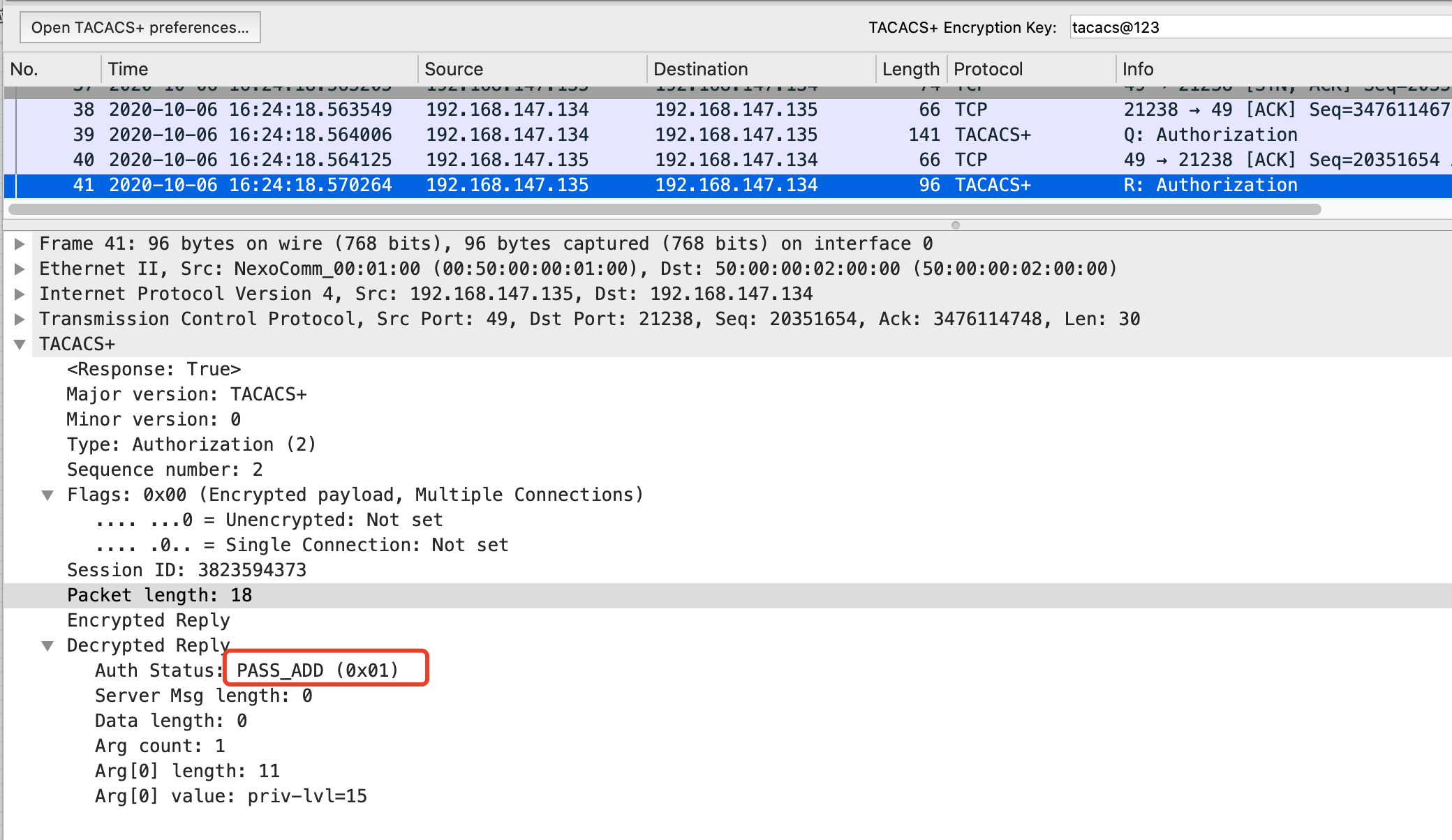
授权回应报文:
Tacacs+服务器收到授权回应请求报文后,会根据配置文件进行回应授权情况,如:p riv-lvl=15。
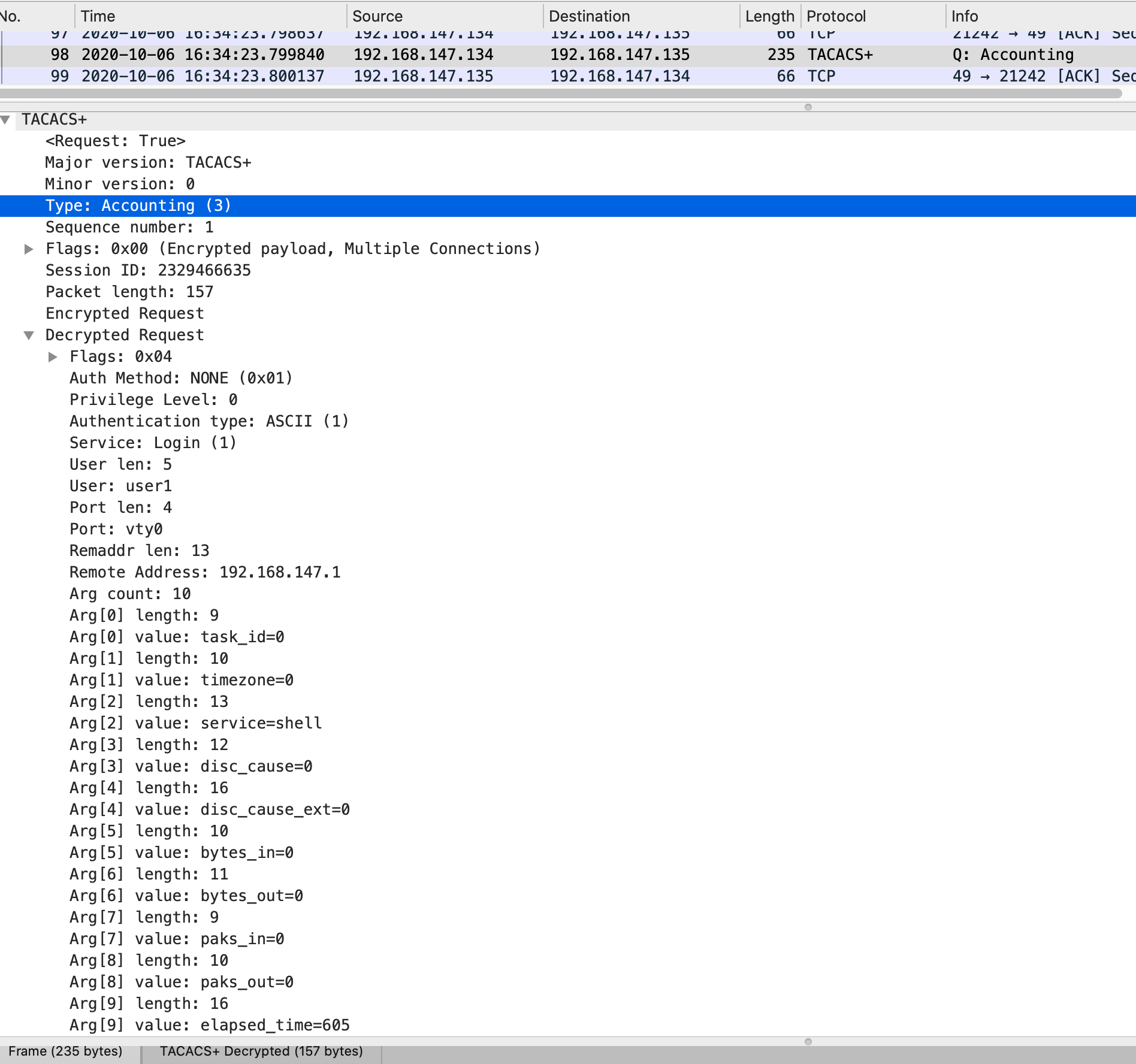
Accounting报文抓包示例:
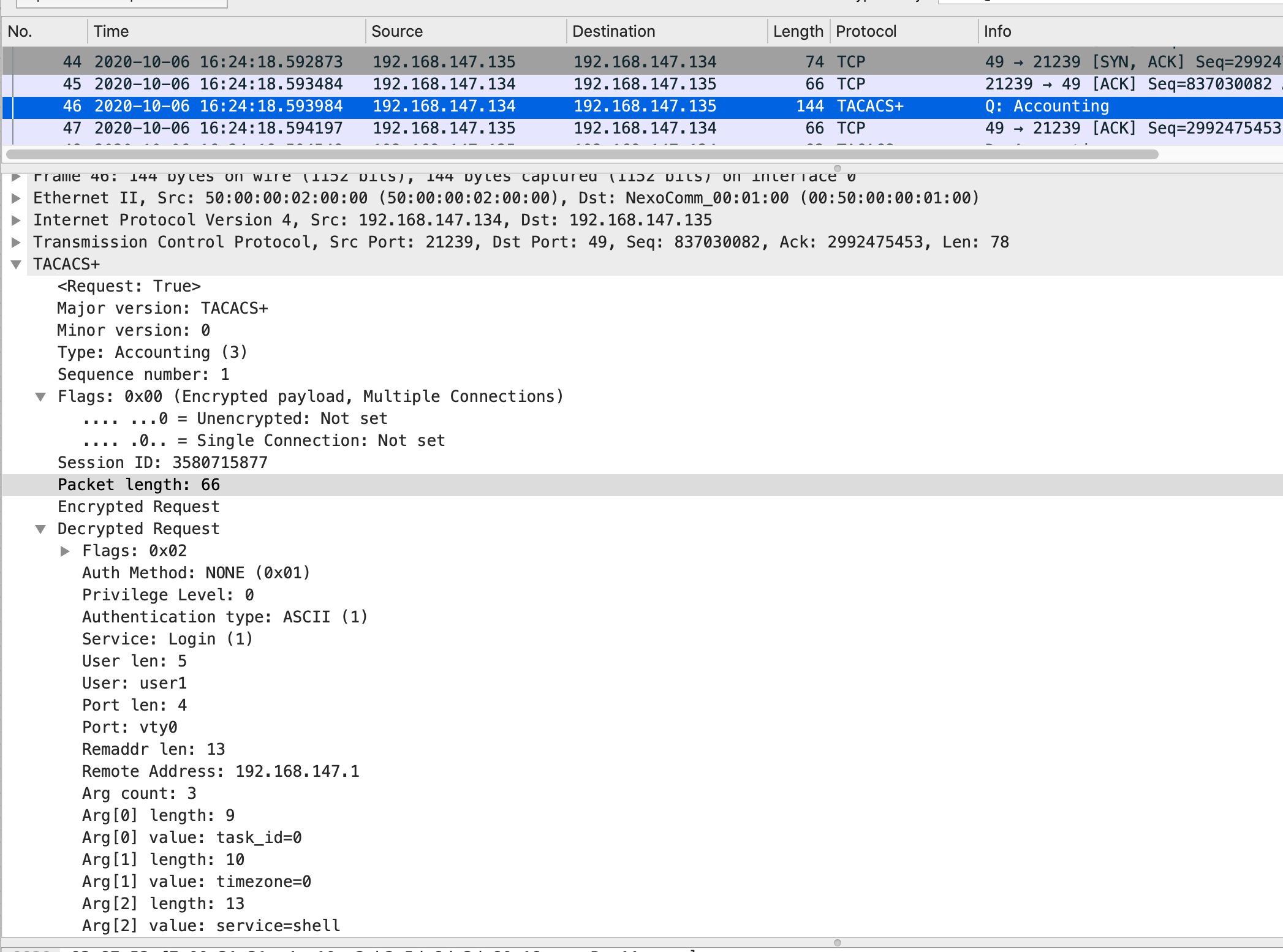
计费请求报文:
在认证和授权成功之后,交换机会发起计费请求报文。
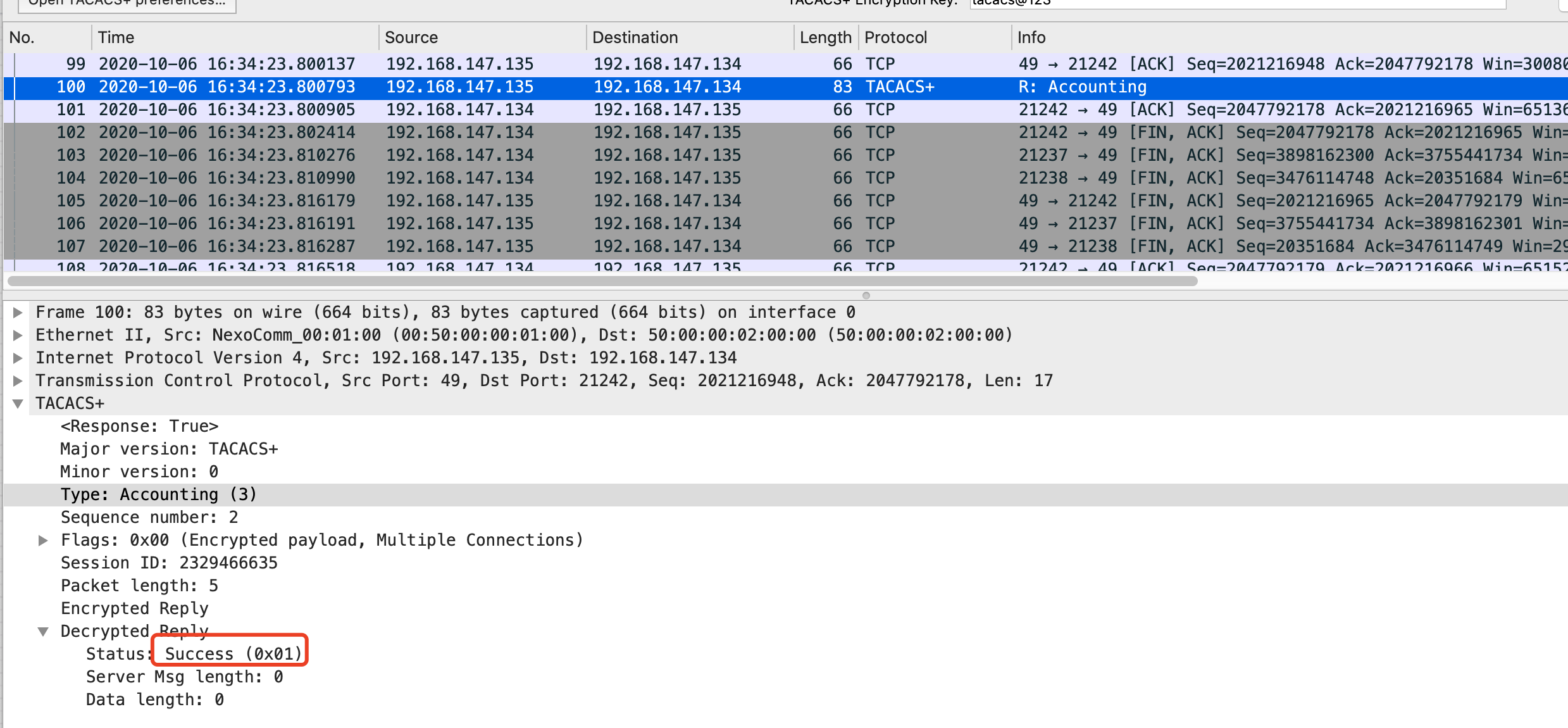
计费回应报文:
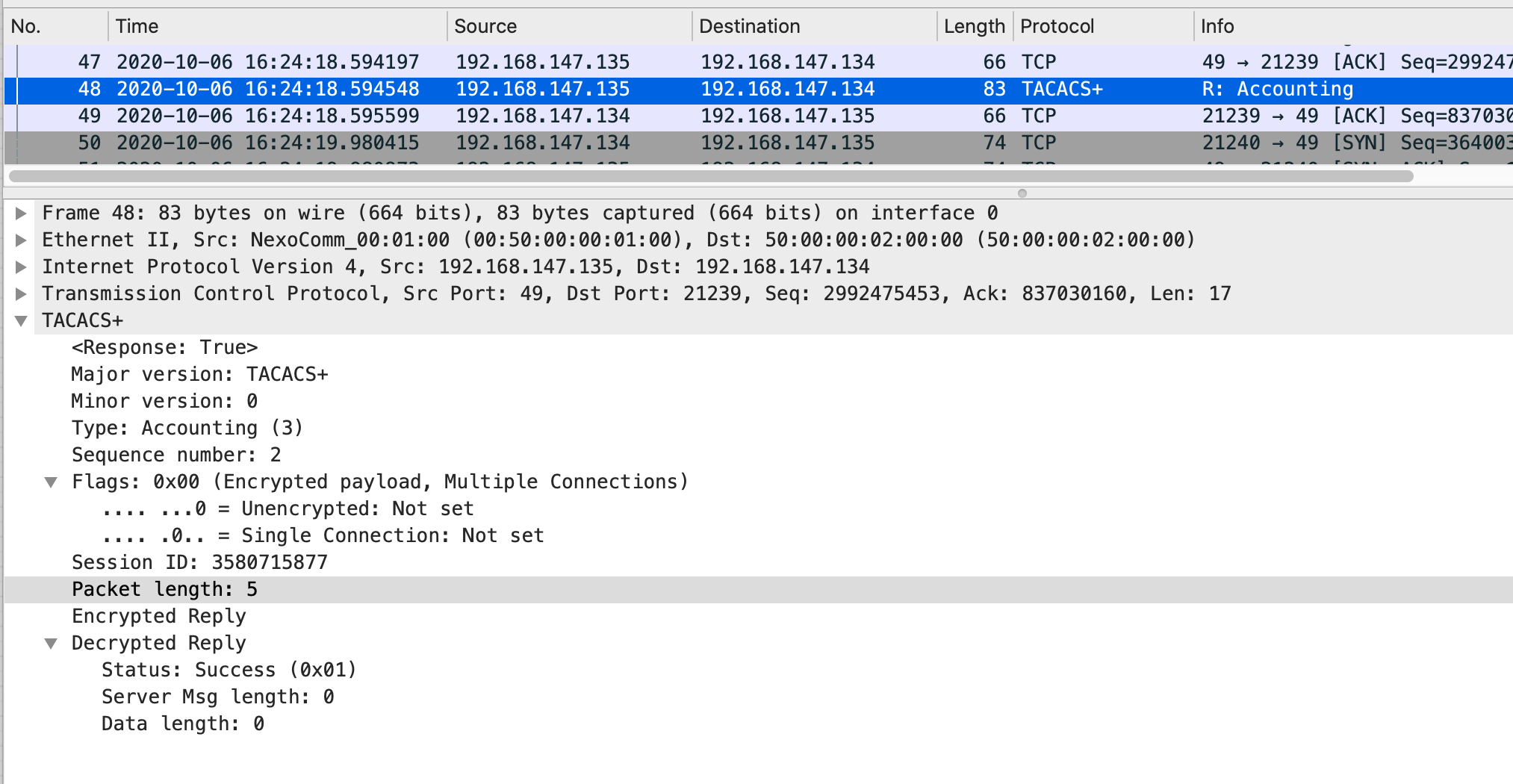
输入dis ip inter bri 后的授权和计费过程抓包示例:
在认证成功之后,在交换机输入的每条命令都会进行如下四个报文交互流程。
授权请求报文:
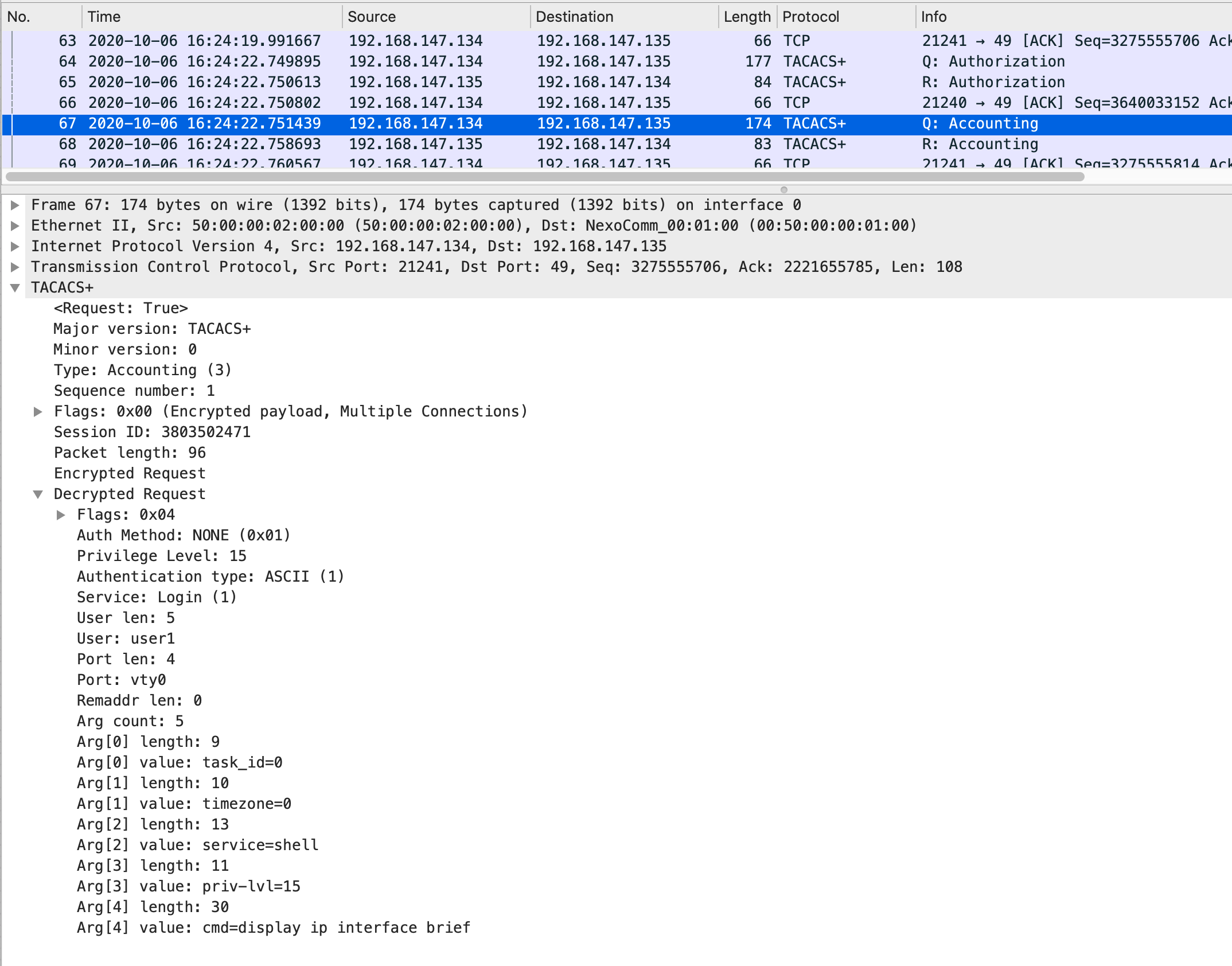
在下图中可看到,当在交换机上输入dis ip inter bri后,交换机会向Tacacs+服务器发起授权请求报文,报文内的dis ip inter bri 会被交换机自动补全,并按空格进行分割,请求多个cmd value,从而发送个服务器进行授权请求。
在Tacacs+服务器上会根据配置文件的授权配置,匹配正则表达等进行判断是否授权。
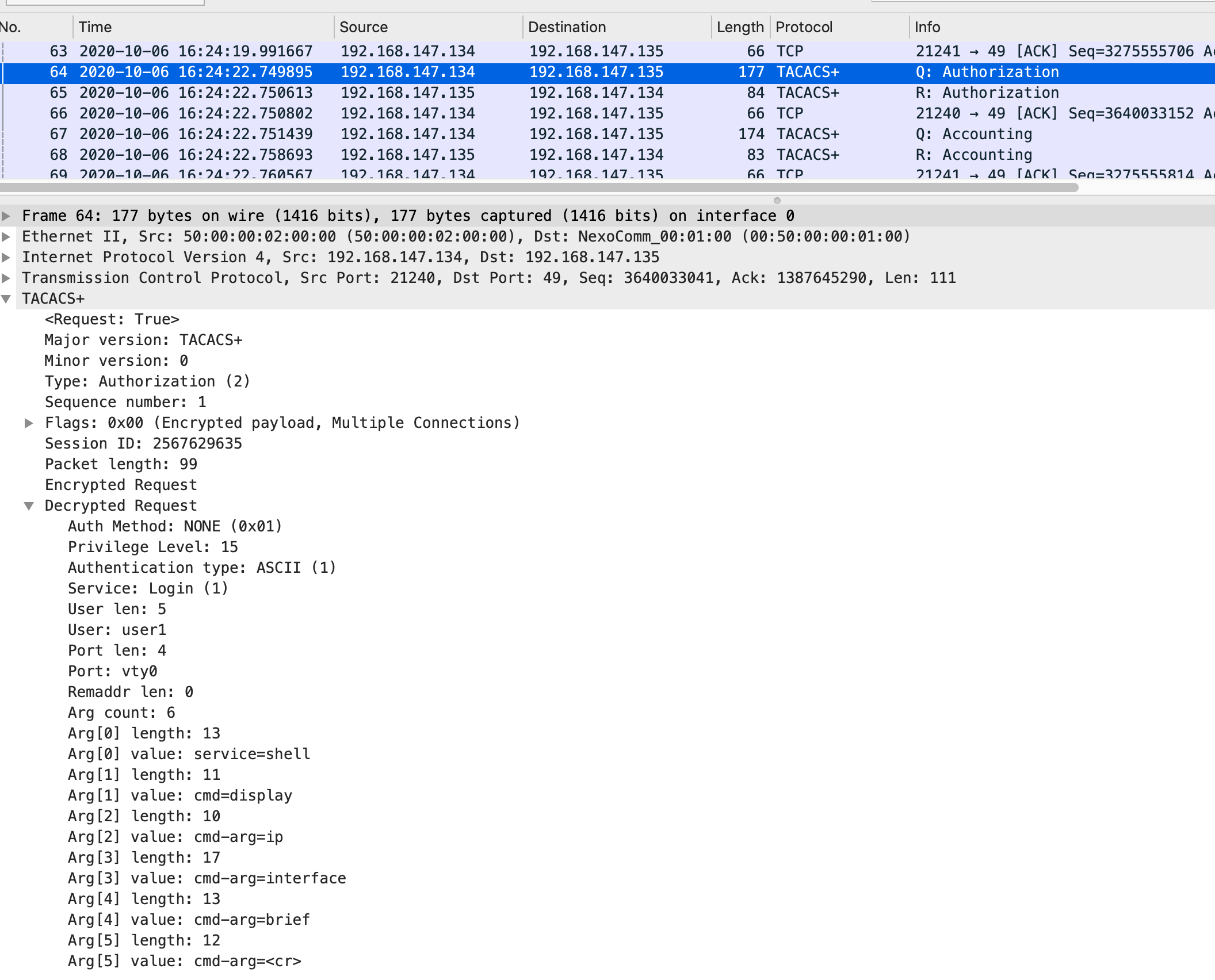
授权回应报文:
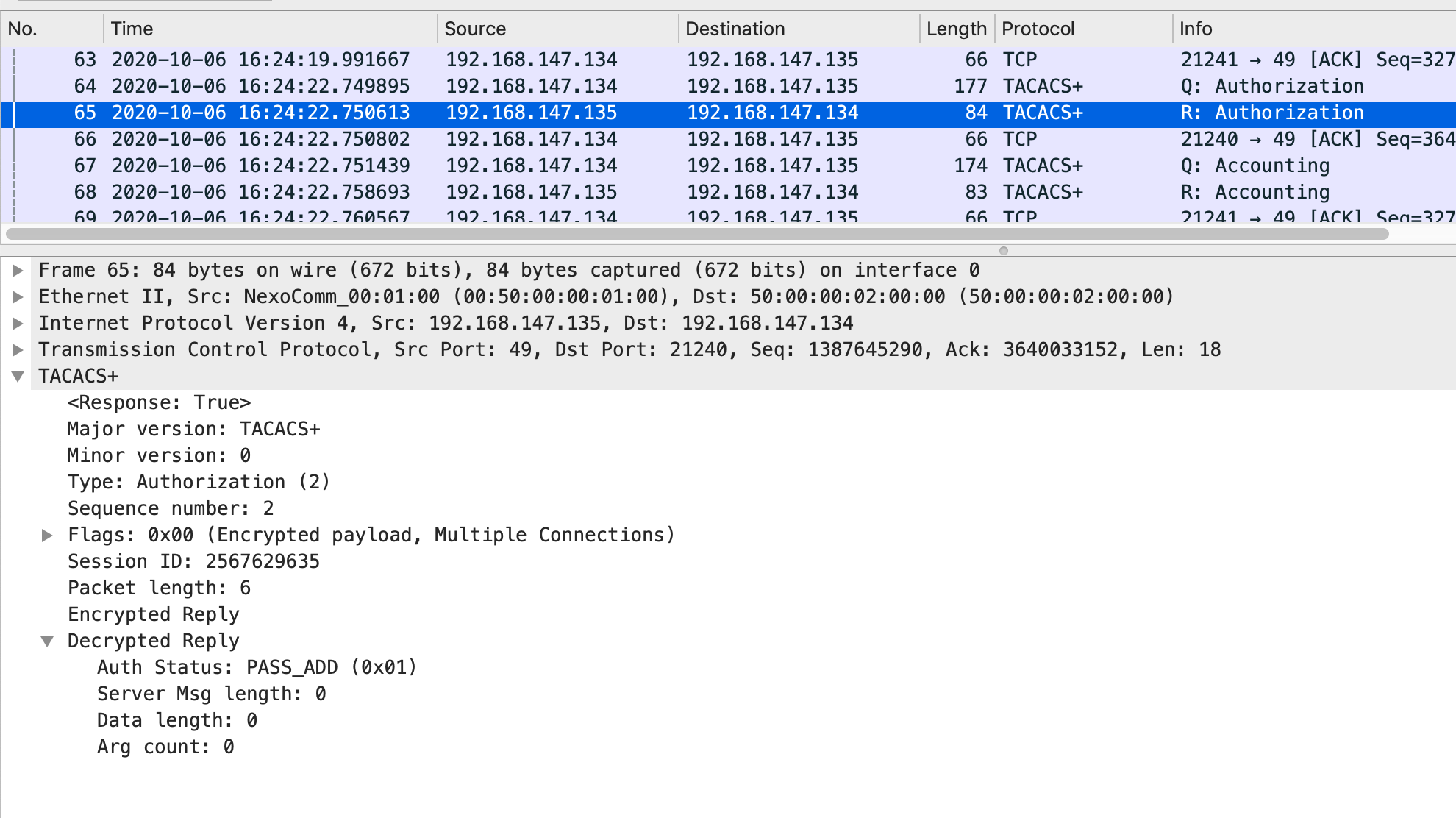
计费请求报文:
在命令被授权后,交换机如果配置了tacacs+计费,会发起计费请求报文,计费请求报文中会携带命令的相关信息,命令字符串,命令级,时区等。
计费回应报文:
Tacacs+服务超时自动端口连接报文抓包示例:
Tacacs+服务器认证,授权,计费日志示例
Access.log:
1 | [root@localhost ~]# more /var/log/tac_plus/a |
authentication.log 认证日志示例:
1 | [root@localhost ~]# more /var/log/tac_plus/authentication/authentication.log |
authorization.log 授权日志示例:
1 | [root@localhost ~]# more /var/log/tac_plus/authorization/authorization.log |
accounting.log 计费日志示例:
1 | [root@localhost ~]# more /var/log/tac_plus/accounting/accounting.log |
其他文章: